The recent incidents of leaks and breaches of cloud-based data have clearly shown that the process of securing data in the cloud is often poorly implemented. Even governments and large organisations who “should have known better” have suffered breaches, despite their considerable resources and awareness.
With the implementation of the EU’s General Data Protection Regulation (GDPR) just six months away, it has never been more important to properly secure data in the cloud. With mandatory breach reporting to be enforced with GDPR, organisations who fail to do so risk reputational damage and hefty financial penalties.
GDPR affects SMEs as well, so all businesses should now be examining their data security practices. This article provides actionable steps to help all organisations from becoming a data breach statistic.
Why infrastructure-level and access-level security is not enough
“The cloud is safer than on-premise…” – this is a common message from cloud providers on the topic of security. After all, cloud providers have hundreds or thousands of security engineers, and collectively they could do a better job than an average system administrator. The cloud provider can also deliver compliance and certification in line with relevant government standards.
It’s hard to argue against that. But then, why do data breaches still occur?
Secure infrastructure certainly mitigates against external threats such as hacking, but it doesn’t automatically result in good data security. It is just as important to mitigate against accidents and mistakes that occur within an organisation. Failing to recognise this leads to a false sense of security.
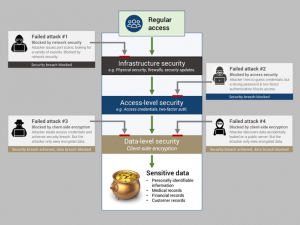
There are three distinct layers of security that can protect data in the cloud:
- Infrastructure-level security: focuses on the infrastructure, such as physical security (e.g. building location and construction; fingerprint scanners for employees) and network security.
- Access-level security: ensuring only authorised users can gain access to the infrastructure.
- Data-level security: ensuring unauthorised parties cannot read or use the data even if they have access to the cloud account – achieved using client-side encryption.
Recent data breaches, such as those experienced by Accenture, Deloitte, and the Swedish Government, are good examples of how a failure at one or more of these layers can have catastrophic consequences. In those cases, there were failures at the access-level security layer – credentials were leaked due to mistakes made within the organisation, enabling unauthorised parties to access the account and data within it.
However, if good data-level security procedures had been implemented, these security breaches should not have resulted in data breaches.
Data-level security via strong, client-side encryption can prevent a security breach from becoming a data breach
Every data breach starts off with a security breach. For example, when the Australian Red Cross Blood Bank leaked the names, addresses and sexual history details of 550,000 blood donors, it was a security breach due to human error. The employee of a third party IT contractor accidentally placed a plaintext database backup onto a public-facing web server.
When properly implemented, client-side encryption is an excellent way to prevent a security breach from becoming a data breach, because an attacker will only see encrypted data.
An extremely effective mitigation against security breaches – whether due to human error or active hacking – is client-side encryption. When properly implemented, this type of encryption is an excellent way to prevent a security breach from becoming a data breach, because an attacker will only see encrypted data.
The role of encryption in mitigating against data breach is also recognised in the GDPR. Specifically, article 32 (1)(a) of GDPR guidelines calls for the “pseudonymisation and encryption of personal data”, taking into account the state of the art and implementation costs. An important benefit of using encryption is that a leak of encrypted data is not classified as a data breach under GDPR. Thus it does not have to be reported, and will not result in financial penalties. Therefore, using encryption is an effective way to mitigate against fines and reputational losses when a breach occurs.
Cutting through the confusion associated with encryption
Unfortunately, encryption is perhaps one of the most underutilised and misunderstood areas in cybersecurity. Due to the number of acronyms (AES, RSA, ECC, TLS), the types of encryption (server-side, client-side) and types of data protected (data in use, data at rest, data in transit), it’s no wonder why many people are confused.
In the context of securing data in the cloud, the two main attributes to consider are:
- Where does the encryption take place – on the cloud server (known as server-side) or on the data owner’s device (known as client-side)?
- Who holds the key – the cloud provider or the data owner?
Not all encryption is the same: why client-side encryption is important
Some cloud providers specifically advertise that they use encryption. However, the devil is in the detail because the types of encryption they offer are often ineffective against common attacks.
- Server-side encryption: If encryption is performed by the cloud provider, it still exposes plaintext (unencrypted) data to the cloud provider, which provides a convenient point for eavesdropping.
- Cloud-held keys: Even worse, when encryption keys are stored by the cloud provider (which is the case in many cloud-based encryption systems), the cloud provider will decrypt and serve up plaintext data to whomever connects to the account – including hackers. This provides no extra security against attackers who compromise the account.
Therefore, the safest way to implement encryption is to choose client-side encryption with client-held keys. This means that the keys are held by the owner of the data, and the encryption/decryption is performed on-premise (and not in the cloud). The cloud provider, therefore, has no way of decrypting the data and serving it to an attacker.
Additional requirements for good cryptographic security
The ideal encryption system should meet a number of additional requirements:
- Transparent encryption – in order to maintain the usability of encrypted data, the encryption should be transparent.
- Encryption of a wide range of data – from data fields, documents, photos and videos, backups, drive images, files.
- Provide long-term security – because quantum computers are expected to break many cryptosystems within 15 years yet records need to be kept secure for lifetimes.
- Allow you to copy encrypted data from one storage location to another (known as ciphertext portability).
- Be designed and peer-reviewed by reputable cryptographers (which counteracts the “snake oil”/lack of trust problem).
The technical reasons for these requirements are beyond the scope of this article, however further details and an expanded discussion about the hidden pitfalls can be found here: comprehensive checklist for client-side encryption and GDPR compliance.
Given these protections are available, why do data breaches still occur?
Dr Ron Steinfeld is a cryptographer and senior lecturer at Australia’s Monash University. He is an expert at cryptographic security for the cloud and has conducted research on a general-purpose encryption system known as ScramFS. He believes the problems with data security stem from the lack of easy and secure encryption solutions. “I think one of the reasons for this [widespread data breaches] is the scarcity of secure cloud storage encryption software that is easy to use and integrated/compatible with commonly used software applications. For that reason, many users store their cloud data unencrypted, or with keys stored on the cloud server. Consequently, any hacker that manages to expose the contents of the server can gain access to the data. Cloud content exposures are not infrequent due to the prevalence of web application bugs and security vulnerabilities, and weak password choices or password reset procedures by users. Encrypting stored user information on the cloud server with a key known only to the user, as is done by ScramFS, should significantly reduce the likelihood of such data breaches.”
Putting it together: a full suite of protection
There is no single silver bullet for securing your data in the cloud. Instead, a multi-layered approach will protect against a wider variety of situations – active hacking and human error.
[clickToTweet tweet=”There is no single silver bullet – How to #Secure your #data in the #Cloud @ScramSoftware” quote=”There is no single silver bullet – How to #Secure your #data in the #Cloud @ScramSoftware”]
Much can be learned from looking at automobile safety. Cars contain multiple mechanisms to keep passengers safe – seat belts, anti-lock brakes, air-bags and electronic stability control. The dramatic increases in passenger safety over the last 50 years have been due to substantial advances in not only the effectiveness of each system but also combining the different systems into a suite that provides comprehensive protection.
An analogous same suite of protection can be achieved for securing data in the cloud. The steps for good security are:
- Secure your infrastructure.
- Secure your access to that infrastructure.
- Secure your data directly using client-side encryption.
It’s now only a matter of months until GDPR comes into effect (25 May 2018). Organisations must move swiftly to secure their data before they become a statistic.
Linus Chang is CEO & founder of Scram Software, which provides world-class cryptography (encryption) tools enabling SMEs and government organisations to easily and affordably secure data in the cloud, and also achieve GDPR compliance for Article 32(1)(a), the “pseudonymisation and encryption of personal data” at all levels.
A computer programmer and entrepreneur from Melbourne, Australia, Linus previously created BackupAssist, an SMB software product which has sold over 170,000 copies to 165 countries including the Department of Homeland Security and NASA.



