Most companies are still busy running risk assessments and tweaking compliance checklists, while attackers are already thinking years ahead.
Cloudflare just added post-quantum cryptography to WARP, its VPN and secure tunnelling service. That means your network traffic can now be protected against future quantum computers that could crack today’s encryption with ridiculous speed.
This isn’t some niche security tweak for enthusiasts. It is the first real step toward defending live internet traffic against the day quantum hardware finally breaks the locks protecting most of the world’s data.
And here’s the problem. Attackers do not need to wait for the technology to mature before they start causing trouble. They can now intercept encrypted traffic and store it until quantum computers are ready to decrypt it. Every transaction, every confidential document, every record moving across your network today could be public tomorrow if you leave your systems on the old algorithms.
Still feeling like you have time to wait?
The Quantum Problem Explained Simply
Modern encryption, such as RSA and elliptic curve, relies on the fact that classical computers are terrible at certain mathematical problems. Factoring large numbers takes too long, so we assume the data is safe.
Quantum computing destroys that assumption. Shor’s algorithm running on a large enough quantum machine can break RSA-2048 or elliptic curve encryption in hours, not decades.
The real threat is this:
- Harvest Now, Decrypt Later: attackers collect encrypted data today
- Quantum Arrives: future hardware cracks the keys
- Your Data: everything from medical records to financial transactions gets exposed retroactively
Changing your keys next year will not save what is already in someone’s archive waiting for quantum technology to mature.
And quantum hardware progress is real. Google, IBM, Microsoft and others are moving fast. Governments are funding post-quantum migration plans. The question is not whether this happens. It is when.
What Cloudflare Just Launched
Cloudflare has added post-quantum key agreement to WARP in hybrid mode. This combines classical and post-quantum algorithms so that if either one is compromised in the future, the other still stands.
Hybrid mode also makes it easier to swap out algorithms later without rebuilding entire systems. That flexibility will matter because the first generation of post-quantum standards is unlikely to be the last. New algorithms will appear. Some will break. Others will replace them.
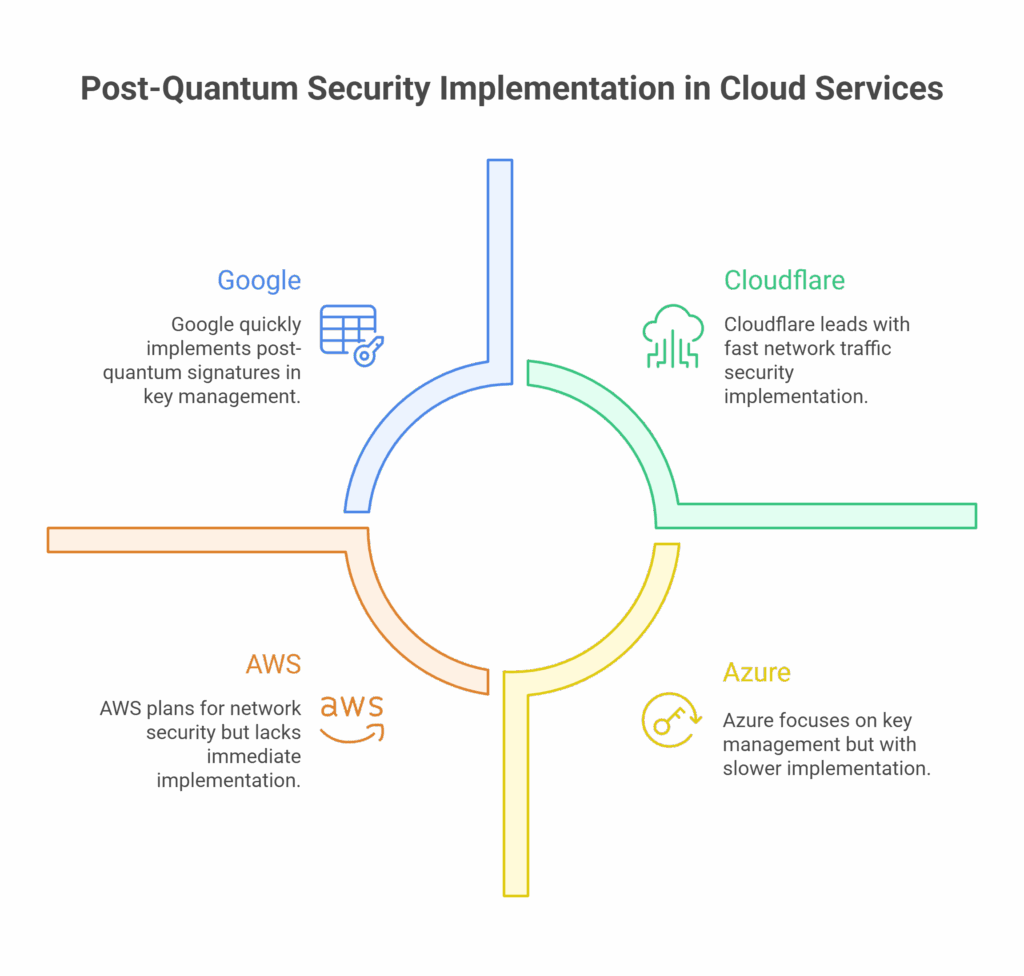
Right now, the comparison looks like this:
- Google has post-quantum signatures in Cloud KMS
- AWS has a migration plan, but no mainstream post-quantum networking yet
- Azure is slower again, focusing on key management
Cloudflare wins for securing network traffic moving right now, not just storage or future APIs.
The Migration Headache Nobody Mentions
Migrating to post-quantum encryption will be messy for most organisations because encryption lives everywhere.
Not just websites. It hides inside:
- VPN tunnels
- API gateways
- load balancers
- legacy partner integrations
- IoT devices still running firmware written years ago
Every one of those systems will need auditing, upgrading, and testing.
Multi-cloud setups make this worse. Each provider is moving at its own speed, using its own tools and terminology. Debugging certificate failures is already painful. Add hybrid post-quantum algorithms across three vendors, and things will break in ways your operations team has never seen before.
The only sensible approach is crypto agility. Build systems that allow you to change algorithms without rewriting code or tearing apart infrastructure.
A Practical Action Plan
Start here if you are responsible for network security:
1. Classify your data. Identify what would ruin you if it became public in ten years.
2. Map where encryption lives. Expect to find TLS endpoints and VPN tunnels you forgot existed.
3. Use Cloudflare or other managed services. They have done the heavy lifting. Post-quantum TLS is running today.
4. Run hybrid algorithms for safety. Classical plus post-quantum in parallel until everything is tested and stable.
5. Design for crypto agility. Never hardcode algorithm choices. Use libraries and services built to swap them easily.
Regulation Will Not Wait
Standards are already here.
- NIST finalised its first post-quantum cryptography standards in 2024
- PCI DSS will inevitably require them for financial data
- GDPR fines will not care whether the attack was quantum or classical
Regulators move slowly until they do not. Leaving old algorithms in production past the warning signs will mean lawsuits as well as breaches.
The Cost of Staying Still
Yes, post-quantum algorithms use bigger keys, more bandwidth, and slightly slower handshakes. But fixing security after a breach is always more expensive than doing it properly the first time.
Crypto agility is not just about technology choices. It is risk management for the next decade.
Final Word
Quantum is not a distant possibility. It is arriving piece by piece, through hardware breakthroughs, government standards, and real deployments like Cloudflare’s post-quantum WARP upgrade.
The tools exist today. The standards exist today. The migration paths exist today.
The only question left is whether you start now or wait until the encryption protecting your business is a museum exhibit and attackers have already made the most of it.




